A group of hackers called The MoneyTaker group has been linked to $10million cyber robbery in many companies. The group of hackers removed overdraft limits on debit cards and took money from cash machines, according to a report by cybersecurity firm Group-IB.
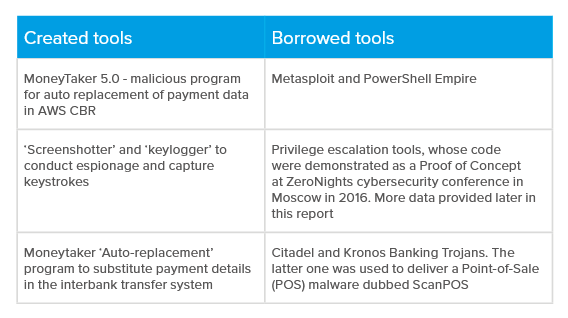
Attackers studied bank networks by stealing documentation files. MoneyTaker avoided detection “by constantly changing their tools and tactics” and “eliminating their traces after completing their operations”, according to a statement from Group-IB.
Russian Speaking Hackers Just Stole $10m from ATMs
Kevin Curran, an independent expert and professor of cybersecurity at Ulster University, said the attacks were “as sophisticated as it gets at this moment in time”. In an interview with BBC, the expert said “It really is perfect in some ways. They’re able to compromise systems and then extract all the documents for how a banking system works so that they have the intelligence needed to produce fraudulent payments.”

Evidence collected by Group-IB suggests attackers intentionally searched and stole internal documentation files to learn about bank operations in preparation for future attacks
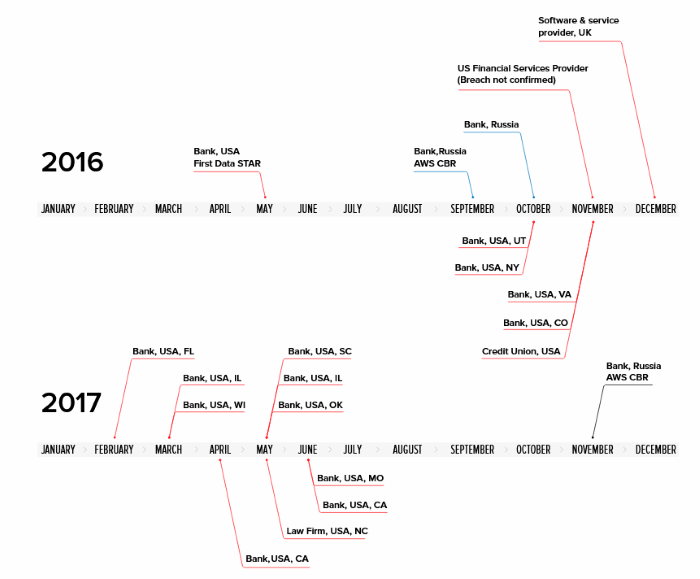
Although yet to be confirmed, the Russian-speaking hackers are suspected of stealing nearly $10m (£7.5m) from 20 companies in Russia, the UK, and US. The hackers stole a documentation for technology used by more than 200 banks in the US and Latin America.
The team of hackers, MoneyTaker – named by Group-IB after the group’s custom malware – has reportedly netted an average of $500,000 in 16 attacks against US companies and $1.2m in three attacks against Russian banks since May 2016.
HOW TO PREVENT FURTHER ATTACKS – Russian Speaking Hackers Just Stole $10m from ATMs.
“Banks are increasingly spending more on security, but the hackers only have to find one way in and they have to protect all the ways in,” said Prof Curran.
Other tactics included changing the servers used to infect banking systems’ networks and using secure sockets layer (SSL) certificates – data files that verify a web browser’s authenticity – that appeared to be issued by big names such as the Federal Reserve Bank.